International Women’s Day 2019 – celebrating and supporting women in technology!
Inclusion, collaboration, and courage – these were the main themes of 5th Annual International Women's Day Talks, presented on March 4th in Toronto. The...
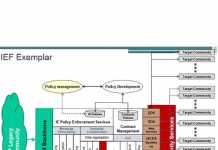
Standards anatomy Pt 2 – Easing consumption to drive adoption
How do standards grow?
“It all starts with standards – they are at the heart of interoperability,” Canada’s Director of Digital Exchange Teresa D’Andrea...
A standards anatomy: building tech norms in government Pt 1
Standards, huh, what are they good for?
Tech standards are widely touted as a panacea for a multitude of sins. Their application will solve interoperability...
Stop IT “Brain Drain” with AIOps
CIO’s face many challenges today – cybersecurity threats, limited budgets, and business transformation issues, to name a few. But is headcount the biggest worry? ...
Huawei Mate 20 Pro review
We call them phones, but when is the last time you heard anyone talking about the telephony capabilities of new mobile devices?
It's been a...
Book review: Hit Refresh
Satya Nadella’s 2018 letter to shareholders and a recent Forbes article describing how Microsoft “blends IoT and edge computing with AI to change the...
Digital identity – Blockchain credentials for the cyberworld
Imagine not being able to prove who you are or where you were born. The World Bank estimates that more than 1.1 billion people...
James Comey squares the circle on “security vs. security”
Former FBI director James Comey claims that celebrity was never one of his career goals. Soft-spoken and thoughtful, he sounds more like the university...
Digital imperative driving Montreal tech
Digitization is the new BPM, jet fuelled by the latest technologies that automate to optimize business processes. It is what managers are now told...
OCE Discovery 2018
Anyone who thinks that Ontario is lacking in innovation needed to have a wander through the 200,000 square feet of exhibit space at the...
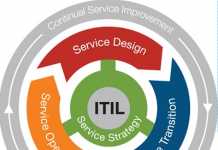
ITIL in 2018 – cloudy days ahead?
Managing information technology has been, and still is, a significant challenge for both enterprises and their service providers. The Information Technology Infrastructure Library (ITIL),...
Agents of change – The BIGPush past gender gaps in VC tech funding
Women do things differently – out of necessity, and to their credit. And nowhere has the “mother of invention” been greater than in the...
Tapping tech for public safety
When we call for emergency services, we don't think about how we'll be taken care of – we just assume it will work. That...
Growing financial inclusion
Let's face it, when it comes to payment methods, we're spoiled. We can use credit cards, debit cards, digital wallets, or even good old...
SMB Summit – the wrap
Panel: Governance, risk, compliance, and cloud security
Michael O'Neil, principal analyst at InsightaaS set the stage for the SMB Summit governance, risk, compliance, and cloud...