The glow surrounding IoT is beginning to fade as organizations come to face one of the key challenges in its implementation – the need to ensure solution security and data privacy. If enthusiasm for IoT continues to mount – in hype cycle visioning and in the CAGRs of analyst forecasting – security issues are dampening the pace at which IoT solutions out rolled out in deployments at production scale, rather than in discrete pilots, across the globe. Like many emerging technologies, IoT presents unique issues on the privacy/security front: in IoT, the stakes are particularly high as the profusion of devices represents an intrusion into the personal realm that is unprecedented, and as failure in critical systems, such as energy or transport, represents an unacceptable risk that may involve production downtime or even loss of life. At the same time, IoT systems are typically composed of a number of components (an integration puzzle in which complexity and uncertainty is introduced at each connection point), deployed at scale (introducing security management issues), and often rely on new, low power sensor technologies which are based on proprietary, baked-in operating systems that remain impervious to bolt-on security efforts. Additionally, perimeter defense mechanisms that have worked in traditional IT environments are likely to have less impact in distributed IoT – the firewall, for example, may have limited impact in mass scale M2M scenarios in which the edge is a shifting one. Secure IoT implementation, then, requires new approaches to system defence and data protection.

As chief strategy officer of the digital device intelligence leader InAuth Mike Lynch explained, “creators of IoT devices at this point don’t really have the security expertise, so the devices may not have the right security embedded to protect them.” Manufacturers of consumer goods like connected refrigerators will have to move into the security business, but since internal product designers may not have the needed technical expertise so security becomes an expensive proposition. In addition, the consumer may not have the necessary education: “What if the manufacturer needs to do a patch on a vulnerability or another update? There are a lot of issues with that process: how is the consumer made aware of that update, is the consumer tech savvy enough to know that they need to update a device in the house that they never thought of being connected to the Internet, do they need to patch some type of firmware? This may be beyond their technical capabilities or their willingness to act.” In some situations, he noted, the manufacturer may not have processes in place to alert consumers when a security issue does in fact arise, as was the case with the October 2016 Mirai botnet attack on Dyn servers.
But even more alarming is that “in the IoT infancy, [manufacturers] are putting out devices where the password is often given away in the manual or in factory default user names and passwords,” Lynch added. “It pretty easy to make malware, to create a botnet and connect to devices where they know that the password is ‘X’.” And while there may be a small proportion of users who are more security aware due to device connection to the Internet, it’s likely that a relatively larger share will not know how to patch or update the device. So in addition to a need for better inherent security in early IoT devices, consumer readiness is a key prerequisite to secure operation of IoT solutions. Ultimately, Lynch believes, consumer awareness around security risk will drive manufacturers to take security issues more seriously.
According to Lynch, there is hope on the horizon in the form of groups that are pushing for adherence to security standards. The Online Trust Alliance, for example, is trying to create awareness around available standards, while advising on good security practices, such as encryption, server monitoring, testing and the use of protection against botnets and brute force attacks – approaches that may be familiar in more traditional IT scenarios. But as Lynch noted, IoT will require additional kinds of security intelligence: if a car connects to a bank, for example, the bank will need to know that it is a car that is connecting. And while there are precedents and technologies that have been applied to ensure this kind of authentication in the mobile world, with IoT, this will need to be extended to multiple new classes of devices.
If is difficult to imagine reliance on consumers’ push for adherence to IoT security standards in this kind of scenario, which requires a level of system knowledge that is beyond what most can manage, consumer inspiration for security delivery in industrial or commercial IoT solutions is similarly difficult to imagine. In many industries, Lynch expects to see regulators lead the way – as was the experience in banking, and will be the case in healthcare or in autonomous vehicles, where danger to life is a clear and present risk.
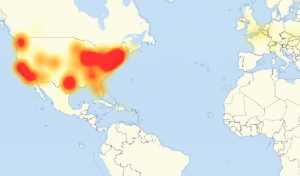
With the connection of billions of devices – in many cases via the Internet – the separation of devices into consumer devices and industrial/commercial categories in terms of their threat impact is largely a moot point. As the Dyn example showed, an attack was launched via cameras of Chinese origin that resulted in Internet failure in many parts of the globe: in other words, the attack surface was a consumer device and the target was industrial. Going forward, attacks may well move beyond the search for financial gain to affect physical systems that we rely on. “If somehow all of our electrical grids are connected through IoT,” Lynch noted, “the relay system between them can be attacked,” and people or institutions deprived of power. “Disrupting your finances is one thing; disrupting your power, or your car or your medical device is a whole new realm,” he added. Unfortunately, these attacks are likely to continue, and as Lynch noted, “they are going to be difficult to defend against because not everyone is thinking about security first, they are thinking more about solution capability.”
If there are no clear answers on how to deliver consistent security across consumer/industrial solutions, Lynch believes there are a number of fundamental approaches to perimeter defence that will be helpful. For example, we will need to develop techniques that will identify that a device is Internet connected, what kind of device is it, and if it has been “seen before.” And while device recognition exists today, it may be that in an IoT world, devices will be identified by traffic patterns. Lynch also advises organizations to put a “cybersecurity playbook” in place so that they understand what steps to take to remediate a DDoS or other attack: “what would you do with your devices if they were part of the ecosystem that was under attack, and how would you shut them down?” A primary goal, he explained, is to identify the source of the threat and differentiate it from other traffic in order to shut down affected machines and contain the damage.
Another option is the deployment of light applications – much like in the mobile world – on the device itself. “Whenever you can be on the endpoint, the security is much more powerful because you can let institutions recognize that device as a unique device that is returning,” Lynch explained. That helps because in the case of a DDoS attack, you know which devices are secure, and which ones to shut down. However, for this to become pervasive, the industry will have to invest in a light operating system with the processing power needed to support the intelligence required. “If the device cannot be patched,” Lynch cautioned, “it will need to be recalled – which comes with its own challenges.”








