In a recent global survey, researchers found that close to half (43%) of IT and security decision makers agree that security is an afterthought when implementing IoT projects, while only half (53%) think connected devices are a threat to their own organizations, even though nearly two-thirds (63%) acknowledged that IoT-related cybersecurity threats have increased over the past 12 months. This seeming inability to connect the dots between increased risk and the need to address organizational vulnerability appears difficult to reconcile; at the same time, it does reflect broad market attitudes that new research from the IoT Coalition Canada (IoTCC) is designed to address. While many organizations remain unclear on tactics and strategy to protect IoT deployments, others assume that traditional approaches to IT security and privacy used by the organization will also manage risks associated with IoT adoption. But is IoT a horse of a different colour? This key question has animated discussion in the IoTCC’s IoT privacy and security working group sessions, and its answer serves as the foundation for analysis in the new report produced by the group, Privacy and Security in the Internet of Things Era: IoTCC Best Practices Guidance.
The IoTCC’s response to this question is a resounding ‘yes’ – though IoT solutions are composed of familiar ICT components and technologies, risks and remediation are different due to the goals and unique character of IoT implementations. In the Definition and Context section of the report, the working group has outlined several ways that IoT introduces new challenges to privacy and security. Solution ‘scope’ is the first issue: IoT is typically deployed is at scale, and as thousands or potentially millions of sensors create new nodes on the network, they introduce additional vulnerability. Scale also creates maintenance issues as security deployment or patch updates are difficult across large numbers of devices. At the same time, the extensive monitoring capabilities enabled by IoT allow unprecedented intrusion into the personal realm through sensor technologies that disregard social norms around privacy, often in ways that are non-compliant with existing regulation. A third challenge emerges around the notion of ‘impact’. Beyond new levels of intrusion into the privacy realm, instrumentation of the physical world means that management and control of critical infrastructure intersects with connected, TCP/IP based networks, increasing risk in environments in which failure could have catastrophic consequences. Compromise of a smart heart pump, a connected car or electric utility could be fatal error.
These new challenges which emerge in IoT adoption have led the IoTCC privacy and security working group to consider the ‘why’ in IoT privacy and security – why work to improve performance in these areas – as well as the ‘how’. As noted in the report, the business objectives driving enhanced privacy and security in IoT – such as ensure uptime for critical infrastructure, reduce potential for regulatory penalty and insurance costs, and maintain brand loyalty and customer/partner trust – are important to the success not only of the IoT project, bus also increasingly obvious factors in maintaining the health of the organization as a whole. As might be expected, the analysis of ‘how’ to ensure IoT privacy and security is a more complex equation that involves the change across social, legal, business culture and technological fronts.
To unravel some of this complexity, the report divides new IoT requirements into “institutional” and “technical” needs, as outlined in the report figure below.
Figure 1. IoT privacy and security requirements
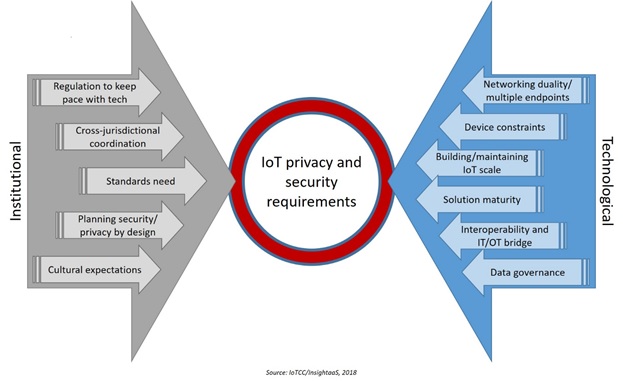
Best practice guidance on these critical requirements is detailed in the main section of the report. InsightaaS urges security professionals, enterprise management in adopting organizations, and IoT innovators to download the full report for more discussion on:
Regulation: “In the IoT era, data will be captured when the individual negotiates public and work spaces, data will identify activity within the private realm, and behavioural assessment will extend out even to the world of mobility though data collected via connected vehicles. As one working group member put it, “it will be Big Data on steroids.”
Cross-jurisdictional issues: “An important aspect of this consolidation will be the creation of standards that can operate – as IoT applications do – on an international basis across jurisdictions. In the absence of global solutions, the working group advises organizations to track the data flow in IoT applications to address any specific privacy and security standards requirements that may be in place for different countries or regions, and suggests that governments build on these initiatives, turning industry guidelines to legislation with the establishment of formal process requirements around third party verification/auditing of standards provisions, while establishing provisions to enforce compliance, and penalties for non-compliance.”
Standards: “Today, market competition has led to the development of multiple, and often competing, data and communications protocols; however, there are also number of initiatives underway aimed at the establishment of standards to address various security concerns. While use of ‘standards’ could take the form of IoT providers and users agreeing on a common architecture in different industries or the use of open source standards, there is now also much activity devoted to the establishment of security protocols for IoT device communication, to threat modeling, the definition of device protection requirements, security architectures, secure software development processes and the testing of security robustness for IoT.”
Planning privacy-security by design: “While it may be possible to secure each individual component, security experts have pointed to the risks associated with a piecemeal approach, and to potential vulnerabilities that appear where one system ends, and another begins. To ensure end-to-end security, the working group advises the adoption of Security and Privacy by Design approaches at the outset of solution development. Securing the endpoint hardware, securing communications – protocol dependencies and what should be provided in terms of firewalls and network segmentation – and securing the supporting compute and storage systems should all be considered upfront to ensure lifecycle protection of data as it traverses IoT systems.”
Cultural expectations: “Security and privacy by design, focusing senior leadership on potential risk and remediation investments, and better cooperation between operational groups such as IT and OT are important cultural shifts within organizations that can encourage better protection in IoT environments. But IoT calls for a broader discussion of cultural transformation, which encompasses recognition of what is at stake from a social perspective, and the alignment of groups that may assume responsibility for change.”
Sensor to edge – new network territory: “While business needs will ultimately determine the appropriate architectures, the working group poses two basic models for assessing security needs: an end-to-end solution, and an architecture in which network termination occurs at the local level (the edge).”
Device constraints: “The complexity involved in traditional IT integration is magnified many times over through the addition of new IoT devices – sensors, actuators and controllers that are often designed with insufficient CPU power to run security software and/or limited communication and battery resources. Purpose-built for specific use cases, IoT sensors represent device diversity in the extreme in terms of capabilities, underlying vendor technologies and even models. However, whether the device is low form factor (low end devices, such as a chip in car, or an insulin pump in healthcare) or high form factor (typically a new device such as a PC or laptop that is very similar across verticals, has compute power and can run an operating system and a controller), it must be possible to address security needs across the IoT solution.”
IoT scale: “The sheer scale of device deployment in IoT scenarios introduces new security management questions. In deployments where thousands of sensors are involved, implementation is typically staged, with security and other management requirements fine tuned on the second or successive phases, a practice that can itself create new vulnerabilities. In large scale deployments, architecture, tools, management, processes all need to be aligned – a project management reality that will take time, even though a staggered approach can entail the creation of new risks.”
Solution maturity: “IoT is a mature market in certain sectors, such as shipping or packaging; however, sectors like agriculture or Smart Cities are now marked by a lot of activity and rapid deployment. A small vendor or startup that is building a connected lightbulb may be more interested in bringing a minimum viable product to market quickly than in ensuring proper security on the device, while smaller companies are less likely to have devoted adequate attention to systems development and the lifecycle approaches that incorporate threat modeling across IoT components. Risk is increased in “fail fast” solutions development, where appropriate levels of security, privacy or regulatory concern may not be given due priority.”
The IT-OT bridge: From a security perspective, the ability to connect “things” is a double-edged sword. Through the convergence of IT and OT (Operational Technology) in industrial settings, IoT adopters can access an array of cloud-based analytics and security tools, which can bring state-of-the-art protection to data and systems. Newer technologies such as Blockchain, the distributed ledger that offers significant new potential to validate transactions, are now touted as panaceas for security risk in IoT. But as the deployment of thousands of IoT sensors multiplies the attack surface, since many organizations do not keep IT and OT separate on different networks, the connection of industrial systems to IP-based networks can introduce new threats, not only to data but also to the operational systems.”
Data governance: “As a result, the location of data capture and storage is a factor that needs to be considered, since different jurisdictions have discrete rules for data management. Beyond privacy issues, massive sensor deployments may collect information that can present new risk to national security – environmental or seismic data, for example, might be manipulated or used for terrorist purposes.”
Sponsors and working group
Creation of IoTCC reports is underwritten by the community’s corporate and individual sponsors. Corporate sponsors include CenturyLink, Cisco, Cogeco Peer 1, CloudOps, Information Builders, Ingram Micro, Avaya, Schneider Electric, Dimensional Strategies Inc., TwelveDot, TA Networks, TIG, ThinkOn and ProServe IT.
InsightaaS and the IoTCC would like to recognize the working group members whose insight and expertise are the source of Privacy and Security in the Internet of Things Era: IoTCC Best Practices Guidance’s exceptional depth and quality (note – links require that you are logged into LinkedIn):
Bill Munson, Strategic research, policy and planning executive, Quantum-Safe Canada, University of Waterloo
Don Sheppard, Consultant on emerging technology, standards advisor, author/writer, ConCon Management Services
Matt Ambrose, Technology Advisory Leader, Private Company Services, PwC Canada
Kelly Friedman, National Counsel, Discovery Services at Borden Ladner Gervais LLP (BLG)
Shankar Somasundaram, Co-Founder & CEO, Asimily
The report also benefits from expert contributions provided by:
Dr. Ann Cavoukian, Expert-in-Residence – Privacy by Design Centre of Excellence, Ryerson
Faud Khan, CEO, TwelveDot
Gnani Gnaneshan, Bioinformatics Scientist, Public Health Ontario
Ryan Freeman, Associate Director, Business & Corporate Development, Yelp
Ted Longley, Former Director, Engineering & Network Operations, ORION
Jay Parkin, Snr. business development rep., production enhancement at Halliburton- Pinnacle Technologies (formerly of Schneider Electric)
InsightaaS thanks each of these thought leaders for their contributions to Privacy and Security in the Internet of Things Era: IoTCC Best Practices Guidance.
Obtaining access to the report
Like all reports produced by the IoTCC and its sister communities (Canadian Analytics Business Coalition, Toronto Cloud Business Coalition, and Vision2Value (V2V): The Economics of Data), Privacy and Security in the Internet of Things Era: IoTCC Best Practices Guidance is available to all interested professionals. Each of the working group sponsors and members listed above is encouraged to distribute Privacy and Security in the Internet of Things Era: IoTCC Best Practices Guidance to their peer and contact networks. The report is also available from InsightaaS: please follow this link and use the code IoTP&Spoint.









Every small business wants to grow and grow quickly. However, any sudden growth in business will always come with its own set of challenges. For instance, a company’s customer service and quality control systems can deteriorate quickly if new demands are not supported by a solid IT base. This puts the company at risk of losing market share to competitors