Tag: #security
Spammers an enterprise unto themselves
The business world operates according to many well-entrenched patterns. Work schedules are defined based on labour and customer demands; a majority of day-to-day business...
The future of encryption
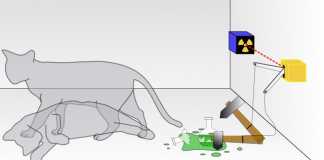
What does a simultaneously dead and not-dead cat have to do with cybersecurity?
Quite a bit, as it turns out. Schrödinger's quantum kitty is the...
CenturyLink takes Managed Security Services 2.0 to APAC
Not all markets are created equal; and not every sales approach will resonate with certain audiences. This was something that CenturyLink kept in mind...
McAfee expands machine learning, automation capabilities to strengthen human-machine teams
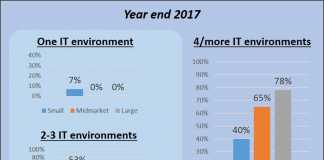
McAfee today released Disrupting the Disruptor, Art or Science?, a new report comparing the role of humans to automation and machine learning in the...
Held for Ransom and WannaCry
Ransomware is big business.
In early May, the UK's National Health Service (NHS), along with hundreds of other organizations worldwide, was crippled by a massive...
Information Builders talks next steps in leveraging IoT data
Presenters at the latest Information Builders breakfast seminar, Powering IoT with an Information Management Strategy, provided a comprehensive view of what it will take...
Secrets of a CISO – Defining the security leader’s development path
A newly-published InsightaaS Industry Brief delivers an insider’s view of the building of a CISO
Of all the challenges facing corporate IT planners, development of...
SDN: networking in the cloud era
Cloud computing is a done deal. Virtually all organizations now use cloud in one form or another: the value proposition of SaaS is no...
Getting them young
We keep hearing that millennials want to work with tools that are familiar, as though that were something new. It's not. Everyone leans towards...
Kantara initiative joins European Trust Foundation
WAKEFIELD, Mass., USA – April 4, 2017 -- Kantara Initiative announced today that it joined the European Trust Foundation to help its non-European Union...
New tools for new breach reporting
Information professional professionals across the country have been considering the ramifications of new requirements in Canada’s Digital Privacy Act legislation slated to come into...
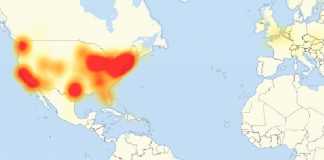
Fat fingers
When a large portion of the World Wide Web suddenly ceased to function recently, it was a wakeup call. Fifty-four of the top 100...
IoT security fundamentals: what risk, why care and who’s driving?
The glow surrounding IoT is beginning to fade as organizations come to face one of the key challenges in its implementation – the need...
Competition or cyber security co-opetition
Competitors in many industries quietly cooperate when it makes sense, even if it's only by establishing and adhering to standards. Just think what the...
Car clouds and data networks – the Ethernet game is on
Celebrated as a “data centre on wheels,” the modern car is more software than ‘hardware’, and kicks off an enormous amount of data that...